10-Days of learning - Day 3 - File Manipulation and System Information

File Manipulation
Messing around with files is a big deal in the world of malware since this is how cybercriminals get their hands on your data, modify system settings, and make sure their malicious software keeps running. Something really important to consider that increases the importance of file manipulation is that in computer systems like *NIX systems, everything is a file, so you can imagine the weight on that.
Stealing Sensitive Information: It infiltrates your computer and grabs important stuff like passwords, financial records, or personal documents. By accessing and altering files, it efficiently gathers and transmits this stolen information back to the hacker.
Modifying System Files: Malware can mess with system files to disrupt normal operations or change how things work. It's like someone coming into your house, rearranging everything, or cutting the power. It might change configuration files or registry entries to take over system functions or disable security features.
Persistence Mechanisms: Malware is like a stubborn tenant who refuses to leave. It uses file manipulation to ensure it keeps running every time you start up or restart your computer. This might involve creating or changing system files so it launches automatically.
Evading Detection: Just like a master of disguise, malware needs to blend in to avoid getting caught. It tweaks system files or registry entries, changing file attributes, timestamps, or names to slip past security software.
Data Exfiltration: Malware doesn’t just steal; it smuggles. By manipulating files, it can quietly package and transmit sensitive data to external servers or devices, ensuring your secrets are no longer safe.
Malware Distribution: Malware spreads like a virus. It uses file manipulation to copy itself to shared network locations or change system files so it can move from one computer to another with ease.
In a nutshell, file manipulation is a key tactic in how malware works. By understanding these methods, developers can create stronger defenses and better security measures to protect against these threats.

File Manipulation with Python
Python provides built-in functions for file manipulation. The open() function is used to open files, and the with statement ensures that the file is properly closed after use.
# Open a file in read mode
with open('malware.txt', 'r') as file:
content = file.read()
print(content)
# Open a file in write mode
with open('malware.txt', 'w') as file:
file.write("This is a malware file!")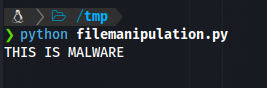
In the first example, we open a file in read mode, read its content, and print it. In the second example, we open a file in write mode and write some content to it.
File manipulation is not only enclosed on the read and modification but also in the creation, this process will be depending of the level of access the process has and the user who executes the malware, meaning, if a user with limited access wants to create a file within a high privileged folder this will not happen, that clarified lets dig into an example of file creation.
import os
# Function to create a malware file
def create_malware_file(filename):
with open(filename, 'w') as file:
file.write("This is a malware file!\n")
# Create a malware file
create_malware_file('malware.txt')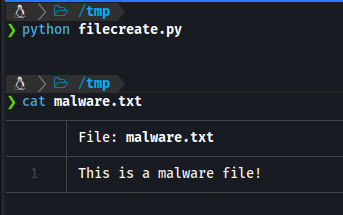
In this example, we define a function create_malware_file() that takes a filename as an argument. Inside the function, we use the open() function with the ‘w’ mode to create a file and write some content to it.
This function can be used in malware development to create files that can be used for various purposes such as stealing sensitive information, persistence, or data exfiltration.

System Information Gathering
System information gathering is a critical part of malware development. It lets cybercriminals collect details about the system and its environment. Here’s why this is important:
Targeting Attacks: Malware needs to know its targets. By gathering system info—like configuration, installed software, and user behavior—malware can pinpoint vulnerable systems or user groups and tailor its attacks accordingly.
Persistence Mechanisms: As mentioned by modifying files the attacker can achieve persistence, malware uses system info to stick around. It can create or tweak system files or registry keys to ensure it runs automatically whenever the system starts up or reboots.
Anti-Analysis Techniques: Malware doesn’t want to get caught. It uses system info to dodge detection by altering system files, registry keys, or environment variables. This includes sneaky tricks like packing, obfuscation, and anti-debugging measures.
Stealth and Covert Communication: Malware likes to blend in. It uses system info to set up hidden communication channels or mimic normal system activity. This might mean altering network traffic, file names, or timestamps.
Stealing Sensitive Information: As mentioned before, malware uses system info to swipe sensitive data. By analyzing system logs and configuration files, it can identify and exfiltrate important stuff like passwords, financial data, or personal files.
In short, the information gathering phase is crucial for creating malware, this helps cybercriminals find their targets and tailor the attacks, to stay hidden, and grab valuable data. By understanding how this works, developers can strengthen their defenses and come up with better security measures to protect against these threats.
Using Python OS library
import os
# Get current working directory
current_directory = os.getcwd()
print("Current directory:", current_directory)
# Get system environment variables
env_variables = os.environ
print("Environment variables:", env_variables)
# Get system version
system_version = os.uname()
print("System version:", system_version)
The function os.getcwd() retrieves the current working directory where the Python script is being executed. This can be useful for understanding the file system context or performing file operations relative to the script’s location. The result is printed to the console for demo purposes.
The os.environ object provides a dictionary of the system’s environment variables. These variables can contain important system configurations, paths, or other sensitive information like API keys or user credentials. The function prints all the environment variables, which can be used to gather information about the system’s configuration.
The function os.uname() returns information about the system, such as the operating system name, node name, release, version, and machine architecture. This information can be useful for identifying the system’s platform, which may be needed for compatibility checks or when performing system-specific operations.
PSutil
import psutil
# Get CPU information
cpu_info = psutil.cpu_times()
print("CPU Times:", cpu_info)
# Get memory information
memory_info = psutil.virtual_memory()
print("Memory Info:", memory_info)
# Get disk usage information
disk_usage = psutil.disk_usage('/')
print("Disk Usage:", disk_usage)
# Get network information
network_info = psutil.net_io_counters()
print("Network Info:", network_info)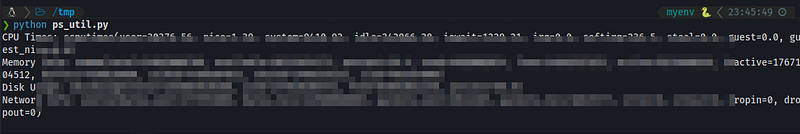
In this example, we're using the psutil library to gather a bunch of system information. For instance, the cpu_times() function helps us get CPU usage data, virtual_memory() gives us memory info, disk_usage() provides details on disk usage, and net_io_counters() lets us see network activity.
The psutil library is packed with functions for monitoring system resources, managing processes, and keeping an eye on network usage. It's pretty versatile and can be used to gather system and environment info, which unfortunately, can also be exploited by malware creators to target systems, dodge detection, and swipe sensitive data. If you want to dive deeper, you can check out the official documentation at https://pypi.org/project/psutil/.
It's crucial to remember to practice ethical hacking and stay on the right side of the law when analyzing and developing malware. Misusing this knowledge is strictly prohibited.
I hope this article gives you a solid understanding of file manipulation and system information in Python, especially in the context of malware development.
